Seeker - Trace Anyone's Location!
First we need to clone this tool from it's Github repository using following command:
git clone https://github.com/thewhiteh4t/seeker
The screenshot of the command is following :

After cloning finished we need to go in seeker's directory, to do that and to see the files we use cd command and ls command so we apply both commands together:
cd seeker && ls
The screenshot is following:

Here we can see the files. First we need to run the installer.sh . This tool also can be run from mobile devices using Termux app. Termux is a terminal emulator with an extensive Linux package collection. If we use a mobile device and using Termux application then we choose the termux-install.sh installer file.
So, the command for our Kali Linux system will be following:
sudo bash install.sh
This will install all requirements to run seeker.
The screenshot is following:

To run this tool we must need to have python3 in our system. Python3 comes preinstalled with Kali Linux but if our system doesn't have Python3 then we should read our this tutorial. To run seeker we use following command:
python3 seeker.py
The screenshot is following:

Here we can see that serveo server (a ssh port forwarding service) is offline so the tool is closed so we manually start the tool on our localhost and forward our localhost to another ssh port forwarding service.
To start Seeker tool manually we run following command:
python3 seeker.py -t manual
The screenshot is following:

Now, we get multiple options. First option is NearYou and second one is GoogleDrive. We also can create a Telegram and Whatsapp group invite. First we create a Gdrive then we will look at the Whatsapp method.
Google Drive Method
We choose option number for Google drive links. Google drive links can look more genuine for the target user. Social engineering techniques will help us to choose a google drive file as per target's interest(it can be movies or lottery or something else). Then we need a shareable link of Google drive.
Then we paste the link and press enter.

Here this is on our localhost sever. We can forward our port 8080 by port forwarding this is may be done by changing our router's settings or we can do it by ngrok or other ssh port forwarding methods. For port forwarding we suggest to our port forwarding tutorial.
For an example we forward our port 8080 by using localhost.run services by using following command in another terminal:
ssh -R 80:localhost:8080 ssh.localhost.run
The screenshot is following:

Now we can send this link to the victim. When victim opens this link he/she can see the Google drive page and that page will prompt victim for location information. If he/she "Allow" this we got all the location information.
Whatsapp Group Invite Method
Same things we can do with Whatsapp method for this we need to choose option 2. After this we need to choose group title and we need to give an image. The image should be relatable with the group's title. We can use any image file but 300x300 images will looks better. We have to give our image path or we can drag and drop our image in terminal to auto fill the path of our image.
Then our localhost server will started as we can see in the following screenshot:
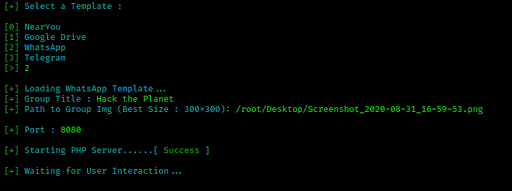
Rest the port forwarding we have given an example in Google Drive method.
Getting the Location
When ever target clicks on attacker's shared link and try to any activity this asks for location permission. If the victim clicks "Allow" we got victim's location.

We got target's device details and location
Now we just copy the Whatsapp group invitation link and send it to victim. We shouldn't worry because this will be a fake webpage exactly like Whatsapp group invitation. The victim will try to connect and we got the location and device info. Victim always get group full notification.

Extra Social Engineering
Now we can send this link to our target but their will minimum chance that our target will click on the link. So we need to do some extra Social Engineering. Suppose we know that our target is jobless and he need some money also target loves to make new friends. In this case we firstly shorten this long URL with bit.ly or any other URL shortener which open the link directly.

Then we send the shorten URL via SMS or any other social media and when our target see the SMS it will looks like following screenshot:
How to be Safe from this
To be safe from this kind of attack we should not open any serveo.net, ngrok or localhost URLs, but if attacker using shorten links we can expand the links from Expand URL's website.



Comments
Post a Comment